Creating Value, Delivering Excellence and Making the Difference
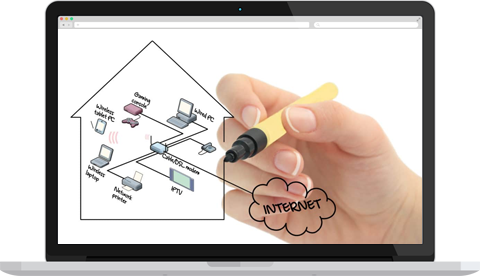
Securing your company’s wireless network from unauthorized access is of paramount importance when it comes to the protection of privacy and critical information of your business. Recommending a 5-step method in this direction:

This policy defines the names and access rights of persons who are allowed to use the wireless network. It can include acceptable use policy, E-mail and communications activities, Antivirus policy, Identity policy, Password policy, Encryption policy and Remote access policy.

This involves encrypting data that travels on the network using not just WEP but also WPA and WPA2 and securing management ports, and authenticating users to be sure you know who is using the WLAN.

Companies can use their staff in the mission of securing the network through informational posters and training about security, passwords, and privacy can help you keep your critical business communications secure.
Installing wireless intelligent protection switching (IPS) devices to prevent unauthorized access points and other wireless threats.
Protect wireless devices with the same security used for the company network, such as firewalls, VPNs, and antivirus software.